Imagine waking up to find every email you’ve ever sent, every website you’ve ever visited, and every conversation you’ve ever had online meticulously recorded and analyzed. This isn’t the plot of a dystopian novel; it’s a reality shaped by mass surveillance. With privacy violations becoming more frequent and severe, understanding the mechanisms behind these breaches is crucial. This article delves into the Fourteen Eyes alliance, its implications for privacy, and the steps you can take to safeguard your personal information.
The concept of privacy has evolved significantly in the digital age. Once considered a fundamental right, privacy is now a battleground where governments and corporations constantly seek to gain the upper hand. The Fourteen Eyes alliance is a prime example of how international cooperation can lead to extensive surveillance networks that compromise individual privacy. By understanding how this alliance operates and its impact on our daily lives, we can better navigate the complex landscape of digital privacy.
What Are The Fourteen Eyes?
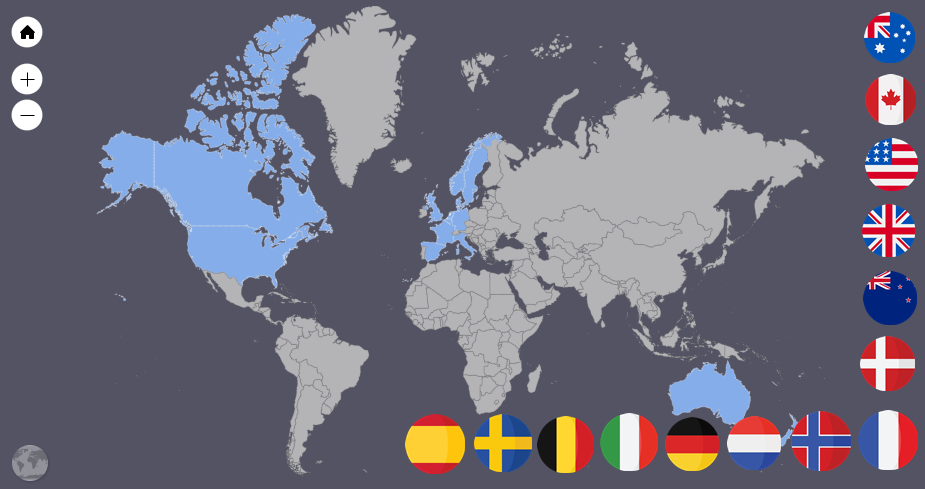
You may be wondering which countries are part of the Fourteen Eyes? The Fourteen Eyes is an international intelligence-sharing alliance that comprises 14 countries: the original Five Eyes (the United States, the United Kingdom, Canada, Australia, and New Zealand), plus nine additional nations (Denmark, France, the Netherlands, Norway, Germany, Belgium, Italy, Sweden, and Spain). This coalition collaborates to collect, analyze, and share intelligence, ostensibly to enhance global security. The alliance’s primary focus is on counter-terrorism, cyber threats, and other national security concerns, but its reach often extends into the personal lives of ordinary citizens.
- 1. 🇺🇸 United States
- 2. 🇬🇧 United Kingdom
- 3. 🇨🇦 Canada
- 4. 🇦🇺 Australia
- 5. 🇳🇿 New Zealand
- 1. 🇺🇸 United States
- 2. 🇬🇧 United Kingdom
- 3. 🇨🇦 Canada
- 4. 🇦🇺 Australia
- 5. 🇳🇿 New Zealand
- 6. 🇩🇰 Denmark
- 7. 🇫🇷 France
- 8. 🇳🇱 Netherlands
- 9. 🇳🇴 Norway
The Fourteen Eyes
- 1. 🇺🇸 United States
- 2. 🇬🇧 United Kingdom
- 3. 🇨🇦 Canada
- 4. 🇦🇺 Australia
- 5. 🇳🇿 New Zealand
- 6. 🇩🇰 Denmark
- 7. 🇫🇷 France
- 8. 🇳🇱 Netherlands
- 9. 🇳🇴 Norway
- 10. 🇩🇪 Germany
- 11. 🇧🇪 Belgium
- 12. 🇮🇹 Italy
- 13. 🇸🇪 Sweden
- 14. 🇪🇸 Spain
Despite its noble intentions, the Fourteen Eyes raises significant privacy concerns. The member countries have extensive surveillance capabilities, allowing them to monitor internet traffic, phone calls, and other forms of communication. This surveillance is not limited to suspected criminals or terrorists; it can potentially target anyone, anywhere. Understanding the scope and scale of the Fourteen Eyes is essential for recognizing the threats it poses to individual privacy.
How Does The 14 Eyes Work?
The alliance operates by leveraging extensive surveillance networks and data-sharing agreements. Member countries collect data through various means, including tapping undersea cables, intercepting communications, and monitoring online activities. This data is then shared among member nations, allowing for a comprehensive analysis of global threats. By pooling their resources and intelligence, these countries aim to create a robust defense against international threats, but this collaboration also means that vast amounts of personal data are constantly being exchanged and scrutinized.
The mechanisms behind this data collection are highly sophisticated. Technologies such as deep packet inspection and metadata analysis enable governments to gather detailed information about individuals’ online behaviors. This data can reveal patterns and associations that would otherwise remain hidden, providing a powerful tool for surveillance. However, the lack of transparency and oversight surrounding these practices raises critical questions about accountability and the protection of civil liberties.
How the Fourteen Eyes Forms?
The origins of the Fourteen Eyes can be traced back to World War II, with the formation of the UKUSA Agreement in 1946, which later evolved into the Five Eyes. This alliance was initially focused on monitoring the communications of the Axis powers and later, during the Cold War, on the Soviet Union. Over the decades, as global threats became more complex, the alliance expanded to include nine additional countries, forming the Fourteen Eyes. This expansion aimed to bolster the alliance’s intelligence capabilities by incorporating diverse perspectives and resources.
The evolution of the Fourteen Eyes reflects broader trends in global security and intelligence. As new threats emerged, such as cyber warfare and international terrorism, the need for enhanced cooperation became evident. The addition of new member countries brought fresh capabilities and expertise to the alliance, enabling it to address a wider range of security challenges. However, this expansion also amplified concerns about the potential for abuse and the erosion of privacy rights on a global scale.

Privacy Concerns About the Fourteen Eyes
Mass Surveillance
One of the most significant concerns associated with the Fourteen Eyes is the potential for mass surveillance. The alliance’s extensive reach means that vast amounts of personal data can be collected without individuals’ knowledge or consent. This surveillance can lead to a profound erosion of privacy, as governments gain the ability to monitor citizens’ every move. The chilling effect on free speech and personal expression is another serious consequence, as individuals may feel compelled to censor themselves due to fear of being watched.
The implications of mass surveillance extend beyond individual privacy. It can undermine democratic principles by allowing governments to exert greater control over their populations. The knowledge that one’s actions are being monitored can stifle dissent and discourage political activism, ultimately weakening the foundations of a free and open society. Furthermore, the vast amounts of data collected can be prone to misuse or exploitation, either by malicious actors within the government or through breaches by external hackers.
Data Retention
The retention of personal data is another critical issue. Once collected, data can be stored for extended periods, often indefinitely. This long-term retention poses significant risks, as it increases the likelihood of data breaches and misuse. Personal information that is supposed to remain confidential could potentially be exposed to unauthorized parties. The longer data is retained, the more vulnerable it becomes to security threats, including hacking and unauthorized access.
In addition to the security risks, data retention also raises ethical and legal concerns. The indefinite storage of personal data can be seen as a violation of individuals’ rights to privacy and data protection. Different countries have varying laws and regulations regarding data retention, and the practices of the Fourteen Eyes members may not always align with these standards. This discrepancy can lead to conflicts and challenges in protecting personal information across borders.
Lack of Transparency About the Fourteen Eyes
The operations of the Fourteen Eyes are shrouded in secrecy, making it difficult for the public to understand the full extent of surveillance activities. This lack of transparency poses a significant challenge to accountability, as citizens are often unaware of how their data is being collected, used, and shared. Without adequate oversight, there is a risk that surveillance powers could be abused, leading to violations of privacy and civil liberties.
Transparency is crucial for maintaining public trust in government institutions. When surveillance activities are conducted in secret, it erodes this trust and fosters suspicion and fear. Greater transparency and accountability are needed to ensure that surveillance practices are conducted in a manner that respects individual rights and adheres to legal and ethical standards. Public awareness and scrutiny can play a vital role in holding governments accountable and preventing abuses of power.
How to Protect Your Privacy from the Fourteen Eyes?
- Use A VPN Outside 14 Eyes
Using a Virtual Private Network (VPN) is a highly effective way to protect your privacy from surveillance. A VPN encrypts your internet connection, making it difficult for third parties, including government agencies, to monitor your online activities. By masking your IP address, a VPN also helps you maintain anonymity online. This additional layer of security can be especially important when accessing sensitive information or communicating in environments where privacy is a concern.
Choosing the right VPN is crucial for ensuring your privacy is adequately protected. Look for VPN providers that have a strong reputation for security and a clear no-logs policy, meaning they do not keep records of your online activities. Additionally, consider using VPNs that are based in countries outside the Fourteen Eyes alliance to further reduce the risk of your data being accessed by member countries.

- Apply Strong Encryption
Encryption is essential for securing online communications and data. By encrypting emails, messages, and other forms of digital communication, you can ensure that only intended recipients can access your information. Utilizing end-to-end encryption tools and services is a crucial step in safeguarding your privacy. Encryption technologies like AES-256 provide robust protection against unauthorized access, making it significantly more difficult for third parties to intercept and decipher your communications.
In addition to using encrypted communication tools, it’s important to encrypt your devices and storage media. Full-disk encryption ensures that all data on your device is protected, even if the device is lost or stolen. This added layer of security can help prevent unauthorized access to sensitive information, providing peace of mind in an increasingly connected world.
- Mind Your Online Behavior
Adopting privacy-conscious online behavior is another key strategy. This includes minimizing the amount of personal information you share online, using privacy-focused search engines, and regularly reviewing and adjusting your privacy settings on social media platforms. Being mindful of your digital footprint can significantly reduce your exposure to surveillance. Simple practices, such as using strong, unique passwords and enabling two-factor authentication, can further enhance your online security.
Another important aspect of privacy-conscious behavior is being cautious about the websites and services you use. Opt for platforms that prioritize user privacy and have transparent data handling practices. Be wary of free services, as they often monetize user data through advertising or other means. By being selective about the online services you engage with, you can better protect your personal information from being exploited.
- Support Privacy Advocacy
Engaging with and supporting privacy advocacy groups can amplify efforts to protect privacy rights. Organizations like the Electronic Frontier Foundation (EFF) and Privacy International work tirelessly to challenge mass surveillance and promote stronger privacy protections. By participating in campaigns and advocating for policy changes, you can contribute to a broader movement for digital privacy. These organizations often provide valuable resources and tools for individuals looking to enhance their privacy practices.
In addition to supporting advocacy groups, consider staying informed about privacy issues and participating in public discourse. Educating yourself and others about the importance of privacy can help build a more informed and engaged community. By raising awareness and advocating for change, you can play a part in shaping policies that protect individual rights and promote greater transparency and accountability.
Facts and Future of The Fourteen Eyes Alliance
Recent developments in technology and policy have further complicated the landscape of global surveillance. For example, advancements in artificial intelligence and big data analytics have enhanced the ability of governments to process and analyze vast amounts of data. These technologies enable more sophisticated surveillance methods, such as predictive policing and behavioral analysis, which can have far-reaching implications for privacy and civil liberties.
Additionally, changes in government policies, such as increased data sharing agreements, have expanded the reach of surveillance activities. International cooperation on issues like counter-terrorism and cyber security often leads to broader data collection and sharing practices. These policies can blur the lines between domestic and international surveillance, making it harder to regulate and control how personal data is handled across borders.
Looking ahead, the impact of the Fourteen Eyes is likely to grow as emerging technologies, like quantum computing and the Internet of Things (IoT), introduce new dimensions to surveillance capabilities. Quantum computing, for instance, has the potential to break traditional encryption methods, posing significant challenges to data security. Meanwhile, the proliferation of IoT devices increases the number of entry points for surveillance, as these devices often collect and transmit vast amounts of data.
Conversely, increased public awareness and advocacy for privacy rights could drive the development of stronger protections and more transparent practices. As individuals become more informed about the risks of mass surveillance, there may be greater demand for privacy-enhancing technologies and stricter regulations. Efforts to promote digital literacy and privacy education can empower people to take control of their personal information and push for meaningful changes in policy and practice.
Conclusion
Understanding the Fourteen Eyes and its implications is crucial in today’s digital age. While the alliance aims to enhance global security, it also poses significant risks to individual privacy. By taking proactive steps, such as using VPNs, encrypting communications, and supporting privacy advocacy, you can protect your personal information and contribute to a broader movement for digital privacy. As technology continues to evolve, staying informed and vigilant will be essential in navigating the challenges posed by mass surveillance.
The balance between security and privacy is a delicate one, and it is up to individuals, governments, and organizations to ensure that privacy rights are not sacrificed in the name of security. By advocating for transparency and accountability, and by adopting practices that protect personal information, we can work towards a future where both security and privacy are respected.