The digital economy has seen a massive surge in subscription-based adult content, with OnlyFans leading the charge. However, this growth has been mirrored by a darker trend: the rise of “leak” culture. For many users, the allure of accessing premium, paywalled content for free is incredibly strong. These leak websites market themselves as a “Robin Hood” service for the internet, promising exclusive content without the monthly subscription fee.
But actually, I can tell you that there is no such thing as a free lunch on the internet. These sites are not run by altruistic fans; they are often the front lines of sophisticated cybercriminal operations. The psychological lure of “exclusive” content is used as bait to draw unsuspecting users into a digital environment where their security is the primary target.
Why are OnlyFans leak websites so popular right now?
The popularity of these sites is also fueled by the increasing difficulty of bypassing official age verification laws. As major platforms implement stricter ID checks, users are driven toward unregulated, unverified corners of the web, often unaware that they are trading their government ID for something much more dangerous: a direct gateway for hackers into their personal devices.
What are the real security risks of “ClickFix” malware?
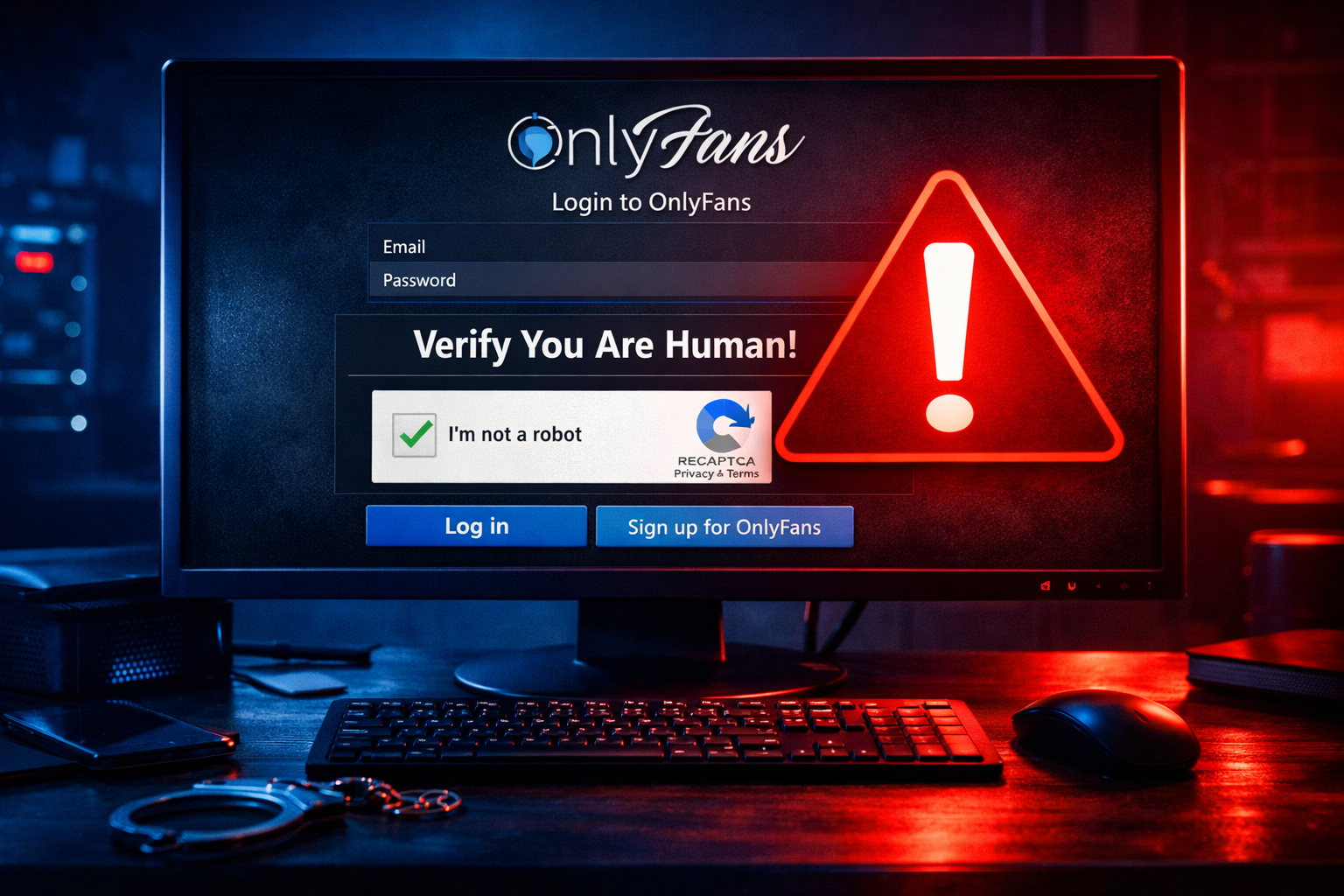
One of the most significant threats we’ve seen in 2026 is the “ClickFix” malware campaign. This is a highly sophisticated social engineering attack that specifically targets users of adult content and social platforms. When you land on a leak site, you might be presented with a fake “I’m not a robot” captcha or a “Verify your age” prompt. Interacting with these elements triggers the download of a malicious .HTA (HTML Application) file.

Once executed, these files can deploy devastating payloads like Epsilon Red Ransomware. This malware encrypts your files and demands a payment for their release, often using ransom notes that mimic high-profile hacking groups to instill fear. Even more insidious is the use of Quasar RATs (Remote Access Trojans), which give hackers complete, silent control over your computer, allowing them to watch you through your webcam or log every keystroke you make.
These attacks often bypass traditional antivirus software because they leverage legitimate Windows components like ActiveX and Windows Script Host (WSH). By the time you realize something is wrong, the damage is often already done, and your most private data is in the hands of anonymous attackers.
Which are the top 8 OnlyFans leak sites to avoid?
If you are tempted to visit a leak site, you should know exactly what you are walking into. These platforms are notorious for their lack of security and their aggressive data-harvesting tactics.
Here are the top 8 sites frequently cited by the cybersecurity community as high-risk zones.
| Site Name | Primary Risk | Security Warning |
|---|---|---|
| Fapello | Aggressive tracking and data harvesting. | Uses advanced fingerprinting to track you across the web. |
| FanslyLeaks | Malicious redirects and pop-under ads. | Frequently redirects to “scareware” sites. |
| Simpcity | Malware-laced “mega-folder” downloads. | Zero vetting for files uploaded by anonymous users. |
| Coomer.party | Massive repository of non-consensual imagery. | High risk of being flagged by ISP for illegal content. |
| ThotsBay | Fake “Verify Age” prompts for malware. | Primary vector for the “ClickFix” ransomware campaign. |
| EroMe | Malicious ads targeting mobile users. | Known for “infostealer” scripts that scrape browser data. |
| SocialGreed | Phishing traps for social media credentials. | Requires “login” to bypass paywalls, hijacking your accounts. |
| Bunkr.is | Trojan-infected file hosting. | Files are frequently flagged for containing hidden Trojans. |
Navigating these sites is like walking through a digital minefield. Even if you don’t download anything, the simple act of visiting them can expose your device to “drive-by” downloads and aggressive tracking scripts.
How do these sites steal your identity and data?
The primary goal of most OnlyFans leak websites is data harvesting. They use “infostealers”—specialized malware designed to scrape your browser for saved passwords, credit card information, and session cookies. This allows hackers to hijack your accounts without ever needing to know your actual password. If you’ve ever wondered how someone “hacked” your social media despite you having a strong password, this is often the culprit.
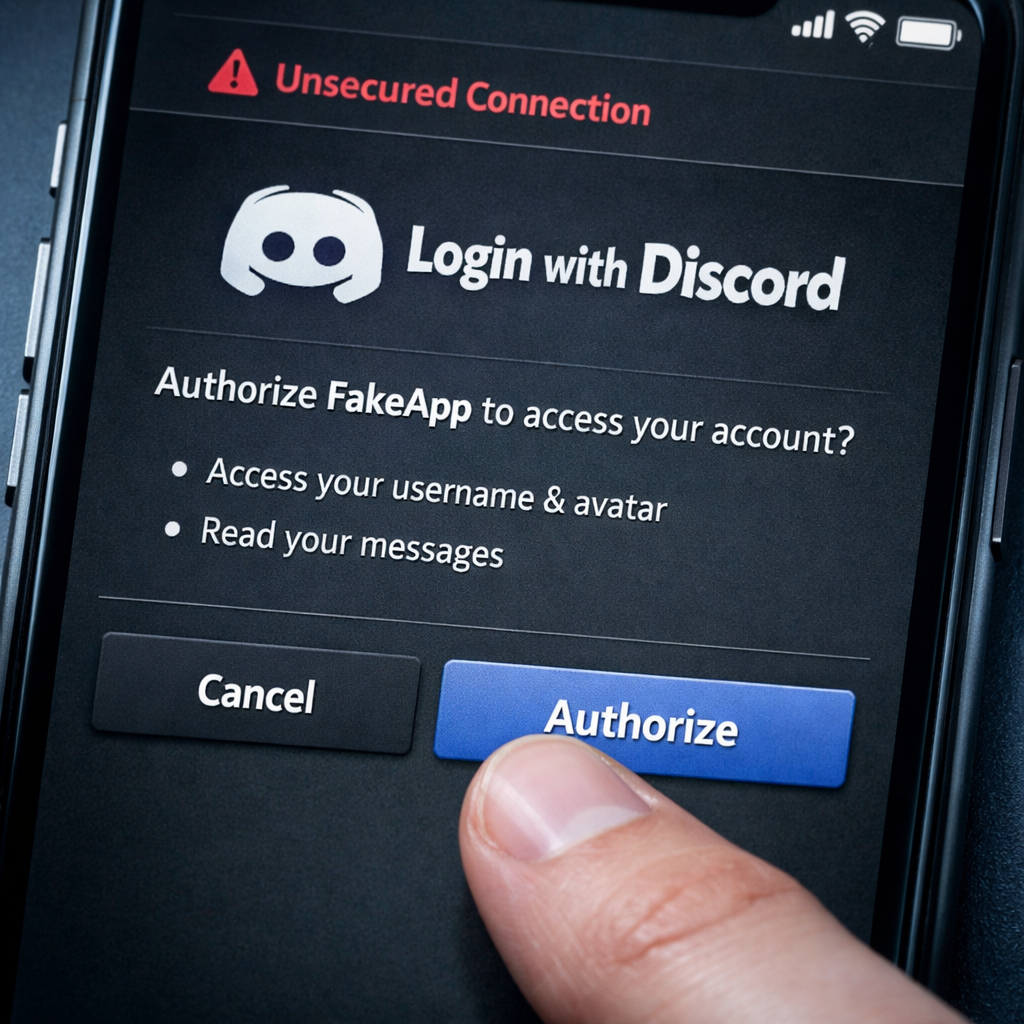
Phishing is another major weapon in their arsenal. You might see a prompt to “Login with Discord” or “Verify with Google” to view a specific video. These are fake login portals designed to steal your credentials the moment you type them in. Once they have access to your primary email or social accounts, they can reset passwords for your bank, your work accounts, and even your cloud storage.
In the cybersecurity community, we call these sites “honeypots.” They attract a specific demographic of users and then systematically strip them of their digital identity. This data is then bundled and sold on dark web marketplaces, where it can be used for everything from fraudulent purchases to long-term blackmail.
Why is a VPN essential for browsing adult content safely?
If you are going to navigate the “wild west” of the internet, you should never do it without a shield. A high-quality VPN is your first and most important line of defense. By masking your real IP address, a VPN prevents malicious sites from tracking your physical location or linking your browsing habits to your real-world identity.
Modern VPNs offer more than just an encrypted tunnel. Features like “Threat Protection” or “CleanWeb” act as a real-time filter, blocking known malware-hosting domains and phishing sites before they even have a chance to load in your browser. This is crucial when visiting leak sites, as many of the infections happen silently in the background through malicious ads or hidden scripts.
Furthermore, a VPN encrypts your entire connection, ensuring that your ISP or any local network snoopers cannot see which sites you are visiting. This layer of privacy is essential for maintaining your anonymity in an era where digital surveillance is becoming the norm.
Who are the top 5 VPNs for security in 2026?
Based on my analysis of current threats and VPN performance, these are the top 5 products I recommend for anyone concerned about their privacy while browsing adult content.
- NordVPN: The industry leader for a reason. Its “Threat Protection Pro” is exceptionally good at identifying and blocking the types of malicious “
.HTA” files used in ClickFix campaigns. - Proton VPN: If you want maximum security, their “Secure Core” architecture routes your traffic through multiple hardened servers in privacy-friendly countries like Switzerland and Iceland.
- ExpressVPN: Known for its “Lightway” protocol, it provides a highly secure and incredibly fast connection, which is perfect for streaming high-definition content without compromising on encryption.
- Surfshark: An excellent choice for those who want a comprehensive security suite. Its “CleanWeb 2.0” feature is specifically tuned to block the aggressive trackers and malware found on leak sites.
- Mullvad VPN: The best choice for those who want to remain completely anonymous to the VPN provider itself. Their account system requires no personal information, not even an email address.
How can you protect yourself from digital exploitation?
Security is a mindset, not just a one-time setup. The “Golden Rule” of the internet still applies: if a site is offering something for free that normally costs money, you are likely the product being sold. Always be skeptical of “verification” prompts that require you to download files or log in with other social accounts.
For those who frequently visit high-risk sites, I recommend using a dedicated “burner” browser or even a virtual machine. This isolates your browsing activity from your main operating system, ensuring that even if you do get infected, the malware cannot reach your personal files or saved passwords.
Finally, keep your operating system and browser updated. Most “silent” infections rely on unpatched vulnerabilities in your software. By staying current and using the right tools—like a robust VPN and a healthy dose of skepticism—you can enjoy the internet on your own terms without becoming another statistic in a hacker’s database.